In November 2010 we introduced, without any depth, the new international consensus standard, “IEC 80001-1 Ed.1: Application of Risk Management for IT-Networks Incorporating Medical Devices—Part 1: Roles, Responsibilities, and Activities.” We briefly mentioned four aspects of 80001 that are communicated unambiguously when managing risk for a medical IT network:
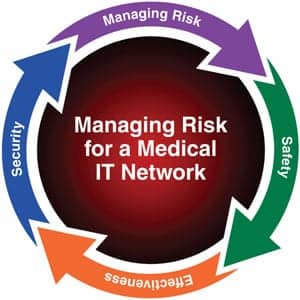
- The three risk components to be managed, in order of priority, are safety, effectiveness, and security.
- The “responsible organization” (typically, the health care provider) is responsible for risk management of all medical devices it places on its IT network.
- Responsible organization includes health delivery organizations of all sizes and types—not just hospitals.
- The responsible organization will need to work closely with medical device manufacturers and providers of other information technology.
As with any standard, much is lost to the reader of the final document who was not involved in the development process. Although the standard itself is one of the shorter consensus standards at only 42 pages, we can still only discuss highlights in a magazine article. As such, this article will discuss the major points in 80001, their importance to the reader, and, as much as practical, explain some of the intent behind them.
By now, whether you are a clinical/biomedical engineer, IT network engineer, clinician, or hospital administrator, the question you should be asking is, “What does IEC 80001 mean to me?” While it would be tempting to give an answer for each of these individuals in the context of their particular roles, the better, simpler answer is to say that 80001 gives you a methodology to engage your coworkers in a process that ensures patients are provided the best care. Notice that we did not say patients are provided the best care at the lowest cost, with the best technology, or even the popular term, “faster, better, cheaper.” That’s because 80001 represents a change to all groups, and a rather large change to some. To all of us, 80001 will mean some amount of confusion; about the best way to implement it, learning how to achieve goals with your co-workers that may appear at first glance to be both counterintuitive and counterproductive, and all those other things you expect from a new initiative. Since confusion typically decreases efficiency, it is reasonable to expect that institutions that embrace the risk management process will see the benefits of implementation far faster than those institutions that struggle with the new process.
We have all seen to some degree all the elements of 80001. We work with them every day. The difference now is in the context. In the past, the old context, we would connect medical systems to the IT network and transport data as part of an ancillary function, such as sending it to a database external to the medical system. If the IT network failed, the medical system continued to function properly and there was no harm. From now on, in the new context, we integrate the medical system with the IT network and expect the IT network to support some primary function of the medical system, such as delivering medical data to a caregiver in a timely and accurate fashion, to an arrhythmia analysis computer, central nursing station, or even a wireless device carried by the clinician. Now, should the IT network fail, the medical system would not function properly, and if not detected in time by the staff, harm could come to the patient and/or it could diminish the clinician’s efficacy in providing care. In other words, the IT network becomes an integral part of the medical system and is no longer a desirable, nice-to-have feature, but a required, critical component.
Establishing a Framework
80001 describes the functions a responsible organization must accomplish to identify, mitigate, and manage the risks associated with putting medical devices and systems on the IT network. First, however, it establishes a common framework by defining several terms and roles. The responsible organization is, quite simply, the entity accountable for the use and maintenance of a medical IT network. The responsible organization is, therefore, responsible for ensuring the key properties of the medical IT network are achieved and maintained. The key properties are, as mentioned earlier, the three risk components to be managed: safety, effectiveness, and security.
According to the standard, there are only two types of networks: the IT network without medical devices connected to it and the medical IT network, in which at least one medical device is connected to the IT network. The 80001 definition of a medical device is nearly identical to that used by the FDA, which is particularly important since virtually all health care institutions already have medical devices connected to their networks in the form of PACS, imaging systems, blood bank equipment, clinical laboratory devices, and clinical monitoring devices, to name a few. In other words, it is almost certain your facility already has a medical IT network as defined by 80001. While some might despair this puts them behind on the learning curve, in reality it provides you with a known example of a medical IT network with relatively low risk. As you begin implementation of 80001 in your facility, you can use these devices to establish a working model and gauge the effectiveness of the risk management methodologies of 80001. It is highly likely those methods found effective for these simple, legacy systems will also work on more complicated implementations or, at the very least, indicate the proper direction to take in managing newly identified risks and more complicated medical IT network combinations.
For 80001 to be successful, the responsible organization must allocate proper resources to the task. To ensure this is done, 80001 names the “person or group of people who direct(s) and control(s) the responsible organization at the highest level” as top management and requires them to create policies for establishing risk management activities. These policies help determine acceptable risks, ensure provision of resources, and identify qualified individuals required to fulfill risk management activities.
Ensuring Risk Management Processes
Top management is also responsible for periodically reviewing the results of risk management activities and ensuring continued suitability and effectiveness of the risk management process toward achieving the key properties.
The risk management process requires a great deal of information from a variety of sources. Top management is also charged with identifying the appropriate people responsible for various tasks and ensuring their cooperation with the medical IT network risk manager (MITN risk manager). These tasks are many, but include the following themes:
- Gathering, analysis, assessment, and storage of information needed for risk management;
- Choice of, procurement, maintenance, technical support, life-cycle management, and use of medical devices;
- Maintenance of medical IT networks;
- Reviewing and accepting residual risk on behalf of top management; and,
- Management responsibilities for medical IT networks and general IT activities.
Finally, top management is required to ensure that anyone performing any supervision, operation, installation, and maintenance of a medical IT network, throughout the network’s life cycle, follows the risk management plan and process. This includes adequately informing these individuals about their responsibility according to 80001, including their responsibility for maintaining the effectiveness of all risk management activities.
From the list of requirements for top management to accomplish, it becomes readily apparent that of the many resources needed in managing risks for a medical IT network, the most important is the MITN risk manager. The MITN risk manager is the “point person” responsible for coordinating efforts and collecting, archiving, and disseminating information between facility personnel, medical device manufacturers, and providers of other information technology. (We will return to these last two shortly.) Top management appoints the MITN risk manager, based on qualifications, knowledge, and competence for risk management, and can be either an internal or external resource.
We have identified the stakeholders, if not explicitly by title, at least by the various required functions and expertise needed to perform the proper management of risks. Let us now turn to the work at hand to be performed by this eclectic group.
The Job Defined
As mentioned in the MITN risk manager’s responsibilities, data must be gathered, analyzed, assessed, and stored. There are three primary sources for this information: the responsible organization itself, the medical device manufacturer, and providers of other information technology. While “medical device manufacturer” is self-descriptive, providers of other information technology describe those OEMs, value-added resellers (or VARs), and third-party providers of all manner of hardware, software, and consulting services used to install or operate an IT network. The types of information required begin to inform the reader of the task at hand. Information is gathered by the MITN risk manager with the aid of a responsibility agreement, comprised of “one or more documents that together fully define the responsibilities of all relevant stakeholders,” which could take the shape of a legal contract.
Medical device manufacturers have long been solely responsible for risks associated with the design and production of their devices. Consequent to their required regulatory review by the FDA, they must fully document their activities, design choices, and reasoning, then store this information in a medical device history file. Since connecting medical devices to the hospital’s IT network defeats the purpose of some of the medical device manufacturers’ risk management activities, in that the medical device manufacturer cannot dictate the network design or operation of the hospital’s IT network, the hospital must now become the entity leading the risk management effort; hence, the term responsible organization. The responsible organization must now replicate for its medical IT network much of the activity previously performed by the medical device manufacturer—that being the risk management process concerning documenting activities, design choices, and reasoning used to create and operate the medical IT network. For the responsible organization, this information is stored in the medical IT risk management file. Other providers of information technology must also now accept some of the risks if they market their equipment, software, or services as suitable for supporting a medical IT network and are likewise expected to provide pertinent information to the responsible organization. Since this information must be provided by the vendor to the responsible organization during the purchase and procurement of the product, the information is described by 80001 as “accompanying documents.”
Although 80001 provides separate lists of information considered to be accompanying documents for both medical device manufacturers and other providers of information technology, there are common themes. The general purpose of the lists is for all vendors to provide instructions and information necessary to ensure the safe and effective use of the medical device. This includes, but is not limited to:
- The purpose of the medical device’s connection to an IT network;
- Technical descriptions and technical manuals;
- Known incompatibilities and restrictions;
- Operating requirements, required characteristics, technical and security specifications, and configuration for the IT network incorporating the medical device;
- The intended information flow between the medical device, the medical IT network, and other devices on the medical IT network;
- A list of the hazardous situations resulting from a failure of the IT network, product corrective actions and recalls, software errors (“bugs”), and cyber security notices (warnings of known security vulnerabilities); and
- Other information identified by the responsible organization as required to ensure the key properties of the medical device.
In addition to the information provided by the vendors, staff of the responsible organization will need to provide additional information such as physical and logical network configurations and client/server structures; applied standards and conformance statements; network security, reliability, and data integrity characteristics; and planned, reasonably foreseeable changes, upgrades, and enhancements.
Once the appropriate information is gathered from the vendors and internal staff, the risk management process can truly begin. The responsible organization begins by documenting its knowledge of the devices and systems to be used in constructing the medical IT network. Risk-relevant asset descriptions are produced to identify hardware, software, data, and other assets, as well as their characteristics deemed to be essential to the intended use of the medical device and medical IT network. All this information is then used in the risk management process, which generates further information used to validate, support, and document decisions during the risk analysis, risk evaluation, risk control, residual risk evaluation, and change-release management processes. For each of these risk management activities, all decisions and their rationale are documented in the medical IT network risk management file.
During risk analysis, available information and data are used to identify hazards to the key properties and estimate associated risks and probability of occurrence of harm. For any instance where the probability of occurrence of harm cannot be determined, the possible consequences shall be considered for risk evaluation and risk control. Risk evaluation is performed to determine if risks are so low that further reduction in the risk is not needed, or if the risks are not acceptable. If the risks are deemed not acceptable, risk control measures must be applied. Risk control measures are applied using any or all of three options. They are, in the priority order listed: inherent design controls, protective measures such as alarms, and information for assurance such as user documentation, warnings, and training. After applying risk controls, any residual risks are evaluated via a risk/benefit analysis and reported to top management for approval.
Changes must frequently be made to systems in order to manage risks associated with new functionality. Any changes made to the medical IT network, whether for normal support of the network or to meet risk control criteria, must be accomplished via a change management and configuration management process. These management processes themselves must include risk management. Final approval before “go live” must be provided by the MITN risk manager and documented in the risk management file.
Risk management of the live medical IT network must be performed throughout its life cycle by monitoring and event management activities. Monitoring consists of observing the medical IT network for emerging risks, effectiveness of risk control measures, and accuracy of original estimations of risk. Event management is used to capture and document negative events, propose changes, track corrective and preventive measures, and report significant findings to the MITN risk manager.
During the entire life cycle of the medical IT network, the medical IT network risk management file is used to contain all documentation pertinent to the medical IT network and decisions regarding it. This file does not necessarily represent a single physical location where all information is stored. The file may contain physical information or pointers to the locations of other information stores.
We hope this high-level overview of IEC 80001 is helpful. As mentioned earlier, detailed coverage is near impossible in a single magazine article. Also, remember that 80001 was designed to allow the responsible organization some flexibility to meet needs that are unique to it. 80001 describes the steps to be accomplished, not a prescriptive checklist of steps to take. Further guidance will come from a set of technical reports now under development. Keep in mind that while 80001 may be challenging to implement, it is both possible and the “right thing” to do.
Rick Hampton is the wireless communications manager, Partners HealthCare System, Boston; and Rick Schrenker is a systems engineering manager, department of biomedical engineering, Massachusetts General Hospital, Boston. For more information, contact .