Rootkits are not inherently good or evil. A set of software programs that work to subvert control of a computer’s operating system from its legitimate operators, rootkits allow continued privileged access while actively hiding their presence from administrators, the operating system, and spyware/malware detection scans. They are more or less facilitators for a payload (or the “data” being transmitted). Rootkits are useful in that they are good at hiding themselves and their payload from the computer system. Since they are often associated with hiding malware, rootkits have become guilty by association, and this is where they obtain their bad vibe.
If you have heard of rootkits, it might mean you have had to battle one. This is a sticky business as it usually means malware has embedded itself to the system root. In UNIX, for example, operating systems run in levels. Each level interfaces with the one above and the one below, and they are called shells or rings. The lowest-level shell is called the root or kernel mode. A number of user mode levels ride on top of the root, each level with less accessibility and fewer privileges (figure 1). The typical user and their top-level applications, such as word processing or e-mail functions, operate mostly at ring three.
Not only are rootkits good at hiding, but they can also be persistent and tough to remove. Most of the time for root-level rootkits the only option is to wipe your drive completely clean and reload your saved good image. This is about as invasive as it gets. The other scary thing is that rootkits are fairly easy to find online. It is not uncommon to see a sophisticated publicly available rootkit hiding some poorly written malware, worms, or attack tools from inexperienced hackers. Somehow I can hear Nicolas Cage sarcastically saying, “Oh, man; that’s just GREAT!”
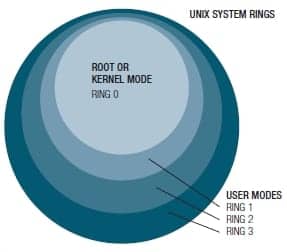
Figure 1. In UNIX, operating systems run in levels. Each level interfaces with the one above and the one below, and they are called shells or rings.
The payload can be any executable, including those that activate only when called upon. Attack tools—like distributed denial-of-service (DDoS), where thousands of zombies (infected computers) are called to browse a particular Web site 400 or 500 times a second—overwhelm the Web site, thereby making it unable to serve its legitimate customers.
It does not have to be all bad news. There have been some legitimate rootkits like Computrace’s LoJack for Laptops intended to foil theft. They are preinstalled in the BIOS—basic input-output system—and therefore persistent over reimaging the hard disc. Unfortunately, researchers have shown that this anti-theft technology system can be turned to malicious purposes if the hacker can find it and is sophisticated enough to rewrite it. Rootkit-infected BIOS usually takes professional help to overcome.
Defining Rootkits
Rootkits are defined in various ways, mostly based on what level they operate or their level of persistence. In general, rootkits can be categorized based on two main facets. First, it depends on whether they are persistent or get wiped away upon reboot (called memory-based rootkits). A persistent rootkit is usually associated with malware. This kind of malware contains code that is executed automatically, either upon system boot or when a user logs in. Therefore, they store code in a persistent manner, like in the registry hive or the file system, then execute without user intervention.
Secondly, rootkits are categorized by where they live and run. These are user-mode rootkits and kernel-mode or root-mode rootkits. User-mode rootkits run in ring three, as seen in figure 1, along with other applications as user, rather than low-level system processes as in the kernel. User-mode rootkits have several possible installation means to intercept and modify the standard behavior of application programming interfaces (APIs). Sometimes they will inject a dynamically linked library (a .DLL file on Windows) into other processes, and are thereby able to execute inside any target process to spoof it or to overwrite the memory of a target application.
Kernel-mode rootkits run with the highest operating system privileges in ring zero. They often do this by adding to or replacing portions of the core operating system in the kernel and associated device drivers. Most operating systems support kernel-mode device drivers, which execute with the same privileges as the operating system itself. This class of rootkit has unrestricted security access, but is more difficult to produce. This kind of code complexity makes bugs all too common, and any bugs in code operating at the kernel level may seriously impact system stability.
Not Just Computers
However, rootkit bugs also can lead to their discovery, as in the “Greek Watergate” wiretapping affair of 2004–2005 when Greek hackers wiretapped Greek government mobile phones. While a complex rootkit, it boils down to disabled audit and transaction logs, patched over commands that list active processes, and blocked checksum verifications. It worked without detection until the hackers issued a rootkit patch that had a bug in it. The bug caused SMS texting to be undelivered, which in turn created an automated failure report. Ericsson (a Swedish telecom company) engineers eventually were brought in, and they found the rootkit, its payload malware, and a list of the government phone numbers that were being monitored. The perpetrators were never found. This is thought to be the first rootkit found in a special-purpose system. Heads up to health care and medical devices!
Since kernel rootkits operate at the same security level as the operating system itself, they can be especially difficult to detect and remove. At this level they are able to intercept and subvert the most trusted operating system operations. Any software, such as antivirus software, running on the compromised system becomes vulnerable. They can also disable event logging to hide evidence of an attack. In these situations, no part of the system can be trusted. (“Oh, man; that’s just GREAT!”)
Evading Detection
There are many methods by which rootkits evade detection. For example, a user-mode rootkit could intercept all calls for a directory listing, whether it is a user call or a system call (eg, Explorer or a command prompt). The object of such calls is to list the contents of a folder or memory area (hard disc, memory stick, CD-ROM, etc). When a directory listing is called, the rootkit intercepts and modifies the output to remove evidence of any rootkit or malware payload entries.
The Windows Native API serves as the interface between user-mode clients and kernel-mode services. The rootkit also can intercept process and file listing calls of the Native API. This prevents detection by scanners that compare the results of a scanner API listing with that returned by a native API enumeration.
Kernel-mode rootkits can be even more powerful, since not only can they intercept the Native API in kernel mode, but they can also directly manipulate kernel-mode data structures. A common technique for hiding the presence of a malware process is to remove the process from the kernel’s list of active processes. Since process management APIs rely on the contents of the list, the malware process will not display in process management tools like Task Manager or Process Explorer. In other words, more sophisticated rootkits work on several shells to prevent their existence from being discovered by system-level or user-level operations. I hate that.
Detection
While typical malware scanning techniques would most likely be ineffective in finding a rootkit, they should still be used to find the malware payload. But the job is far from done at that point since the rootkit will just reload it from its cloaked locations. You still need to remove the rootkit itself. The best and most reliable method for operating-system-level rootkit detection is effective because you run the hardware from an alternate trusted source like a rescue CD-ROM or flash drive. Rootkits cannot actively hide their presence if they are not running. Shut down the computer suspected of infection, and then check its storage contents while running from an alternative trusted medium. Compare results with a known good listing to spot rootkit files. Manual removal is difficult and tedious, so use a special rootkit finder/eradicator to do the job. I think you also have to thrust a wooden stake through its heart during daylight hours. Rootkits are the most invasive of malware delivery and operation schemes. While interesting to explore, I hope your investigations stem from magazine articles rather than firsthand experience!
Jeff Kabachinski, MS-T, BS-ETE, MCNE, is the director of technical development for Aramark Healthcare Technologies in Charlotte, NC. For more information, contact .





