By Brian Wells
They pump insulin to treat diabetics, provide electrical stimulations to regulate the human heartbeat, monitor vital signs, and “feed” patients with the nutrients and drugs they need. But they have also emerged as primary targets of hackers.
They are medical devices—the pumps and pacemakers and other gadgets that have grown increasingly linked to such in-demand and developing technologies as the cloud and the Internet of Things (IoT). In this case, IoT innovation serves as a double-edged sword: while it dramatically advances the capabilities of these devices, it also introduces a wealth of new vulnerabilities that are often difficult to identify and remove.
When hackers take advantage to compromise a device, they can lock down a hospital’s data and “hold” it for ransom, and even manipulate a machine to deliver a lethal dose of drugs, to cite just two of many potentially devastating but realistic scenarios.
Over the last two years, published research and new developments related to medical devices—as well as the healthcare industry and cybersecurity overall—illustrate the rising risk of significant and damaging attacks:
- Eighty-one percent of health care organizations have had their data compromised over a two-year period, according to survey research from KPMG, and nearly one-third of industry executives rank medical device threats as a top information security issue.
- More than one-third of organizations that operate or otherwise use IoT-connected medical devices have experienced a cybersecurity incident within the past 12 months, according to survey research from Deloitte. Top challenges related to the protection of the devices include the identification and mitigation of the risks of fielded and legacy-connected devices (as cited by 30.1% of survey respondents); the need to embed vulnerability management into the design phase of the devices (19.7%); incident monitoring and response (19.5%); and a lack of collaboration about threat management throughout the connected medical device supply chain (17.9%).
- The vast majority of healthcare providers spend on average less than 6% of their IT budget on security, or less than one-half of the 12–15%that the finance/banking sector and federal government spends, according to research from the Healthcare Information and Management Systems Society (HIMSS) Analytics and Symantec.
- In February 2016, the Department of Health and Human Services (HHS) reported that nearly 112 million personal health records were breached in 2015, up sharply from an estimated 1.8 million records the year before. The healthcare industry accounts for an astonishing 88% of all ransomware attacks, according to research from NTT Security.
- In May, researchers from WhiteScope analyzed seven pacemaker products from four different vendors and found more than 8,000 vulnerabilities that hackers could exploit. The researchers discovered unencrypted patient data stored on two pacemaker programs, with one that included names, phone numbers, medical information, and Social Security numbers. “Despite efforts from the FDA to streamline routine cybersecurity updates, all programs we examined had outdated software with known vulnerabilities,” the researchers wrote in a blog post about the study.
- In April, The Hill reported that the FDA is becoming increasingly concerned about vulnerabilities in medical devices and is coordinating with federal agencies as to how to respond to a major hack. “(We) should consider the environment a hostile environment, there are constant attempts at intrusion … and they have to be hardened,” said Suzanne Schwartz, associate director for science and strategic partnerships at the FDA’s Center for Devices and Radiological Health.
- Testimony in April from a top Merck & Company cybersecurity executive before the House Committee on Energy and Commerce’s Oversight and Investigations Subcommittee validated the concerns. “In just the last few years … we’ve seen more than 100,000,000 health records of American citizens (compromised or threatened) in a couple of well-publicized incidents,” says Terry Rice, vice president of IT risk management and chief information security officer at Merck. “We have seen how software vulnerabilities in insulin pumps and pacemakers can be exploited to cause potentially lethal attacks. And we have witnessed entire hospitals in the United States and the United Kingdom shutting down for multiple days to combat ransomware infections in critical systems. Unfortunately, I believe these incidents underrepresent the risk we are facing.”
- A number of major incidents further underscore the urgency of the issue, including the following three: In September 2017, Abbott announced a voluntary recall impacting 465,000 pacemakers due to a possible hacking threat. In October 2016, Johnson & Johnson sent an official notification to 114,000 diabetic patients that a cyber attacker could exploit one of its insulin pumps, the J&J Animas OneTouch Ping, disabling the device or altering the dosage, according to the company. In July 2015, the FDA recommended to hospitals not to use Hospira’s Symbiq infusion pumps—medical devices that deliver nutrients, drugs, and additional fluids into a patient’s body—because of a vulnerability that could enable a hacker to access the pump and change the dose.
Beyond the numbers, testimony, and publicized incidents, organizations across the board are struggling to overcome these common barriers to operational safety and data protection:
1. The majority of devices are not connected to an organization’s internal network. In one sense, actually, this is a good thing. If a device isn’t connected, adversaries can’t target it to steal the enterprise data “crown jewels.” However, disconnected devices cause immense, logistical hurdles.
A hospital could rely upon literally thousands of them, and they’re highly portable as nurses and other staffers move them from room to room. Thus, if a vendor issues a recall, it’s very difficult to track them all down and either repair/patch them or ship them back to the vendor.
2. Devices (whether connected to the network or not) serve a critical, medical purpose. Even if there is a recall, some hospitals might hesitate to respond because they have no other available products that support the same, patient-focused needs.
3. Devices frequently do not run on standard or current versions of operating systems, like Windows, macOS, or even Linux. They’re vendor-created, which leaves healthcare organizations at the mercy of the vendor to update them for patches. But vendors do not always view patches as a top priority and/or cannot keep up with the pace of the fast-shifting threat landscape. Nor does it help that there is no industry standard to follow to lend clarity and concise direction as to how to proceed with preventative, protective measures.
4. Government approval leads to a “hands-off” approach. The FDA certifies all devices, and that results in a false sense of comfort, i.e. “if the FDA thinks the devices are OK, then they must be fine.” Subsequently, organizations are reluctant to adopt vigilant and proactive strategies with regard to threat monitoring, identification, and mitigation.
All of this may sound overwhelming, and that’s perfectly understandable. Fortunately, there are proven best practices that can help you effectively manage the risk.
As indicated, most devices are not network-connected, but this shouldn’t last, as demand for big data/analytics, related to the data generated by attached medical devices, continues to grow. Hospitals will turn to devices to collect and analyze information about vital signs, symptom indicators, patient histories, etc.
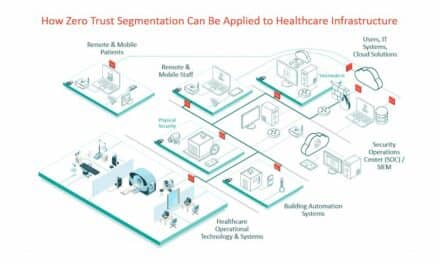
To do so while safeguarding the network, you should consider the implementation of a comprehensive network segmentation architecture. Simply stated, a segmented architecture creates an entirely separate network environment, solely designated for medical devices.
There is no connection whatsoever to non-device related data. Therefore, if attackers compromise a device, there’s only so much harm they can do, because the device is “walled off” from everything else within the enterprise.
Similarly, you must pay heed to wireless devices, which are easily hacked by any person in a doctor’s office or hospital who can access transmission points between the device and the server. With this, they can pull device data and “disguise” themselves as the device to gain entry to the network and to do, well, lots of bad things.
That’s why you’ll need a segmented network for wireless devices, which operates like your non-wireless device segmented network as described above. Such a segmented environment must incorporate the highest level of encryption—much more so than what we accept for our phones—to ensure airtight protection.
Lastly, whether a wireless or non-wireless product, you should deploy a device discovery and network access control solution to reduce the chances of a newly attached, non-segmented device opening up an attack vector within your network. These technologies constantly monitor the networks for new devices.
They could, say, identify an infusion pump that was just “plugged in” and immediately shut it down via a virtual firewall, until the IT team can reroute it to the segmented network. This capability proves critical especially for healthcare organizations that conduct research or have an abundance of satellite offices, as IT may have not yet set up a number of these settings for device segmentation.
When it comes to medical devices, we cannot “put the genie back in the bottle.” It would be inadvisable, after all, to ignore or dismiss how IoT, the cloud, big data/analytics and a host of other innovations open up limitless possibilities in terms of the good these devices can do.
But we must move forward with our eyes wide open, with full awareness of how cyber adversaries can make a “worst case scenario” a reality. Through segmentation, encryption, and virtual firewall-based monitoring and detection, you keep the adversaries in check and allow the devices to enable you to do what you do—help patients live longer and healthier—better than ever.
Brian Wells is director of healthcare strategy for Merlin International, a leading provider of system integration services and solutions that enable the U.S. federal government to better meet mission requirements and challenges.





Conflating data theft/ransom and malicious device interference confuses rather than illuminates the issues. Data theft is real although it is likely that everyone’s personal information has already been stolen. Malicious device interference is a maybe, but the notion supports self-servicing consultants with a business model of declaring there is a big problem, and that hiring them is part of the solution.
Is Merlin International a certified small business enterprise as asserted? Unlikely.
Is the $80 Million Cybersecurity contract award a small business set aside????
Was the VA the agency awarding the contract?
Companies the bid on the contract?