While cybersecurity alerts raised concerns about a potential backdoor linked to a Chinese IP address, researchers uncovered a different—but still serious—security risk.
Summary:
Recent alerts from CISA and the FDA raised concerns that the Contec CMS8000 patient monitor and its white-label variants might contain a backdoor communicating with a Chinese IP address. However, Claroty’s Team82 investigated the device and concluded that the issue is not an intentional backdoor but rather an insecure design flaw that exposes hospitals to cyber risks. The device’s firmware update process uses an insecure protocol and a hardcoded IP address, which could allow attackers to introduce malicious updates. Researchers urge healthcare providers to strengthen cybersecurity measures, as these vulnerabilities could compromise hospital networks and patient data.
Key Takeaways:
- Not a Backdoor, But a Serious Risk: While initial alerts suggested a hidden backdoor, researchers determined the security flaw stems from poor design, making hospital networks vulnerable to attacks.
- Insecure Firmware Updates Pose a Threat: The patient monitor relies on an unprotected update mechanism using a publicly routable IP address, increasing the risk of malicious firmware injections and data breaches.
- Hospitals Must Strengthen Cyber Defenses: Experts recommend network segmentation, firmware validation, and cybersecurity training for IT and clinical engineering teams to mitigate the risks posed by insecure medical devices.
On Jan 30, The Cybersecurity Infrastructure & Security Agency (CISA) released an alert, complemented by a notification from the US Food and Drug Administration (FDA), suggesting that the Contec CMS8000 patient monitor and OEM white-label variants contain a backdoor communicating to a Chinese IP address.
Team82, Claroty’s research arm, investigated the firmware and reached the conclusion that it is most likely not a hidden backdoor but instead an insecure/vulnerable design that introduces great risk to the patient monitor users and hospital networks.
This conclusion, according to Team82, is mainly based on the fact that the vendor—and resellers who re-label and sell the monitor—list the IP address in their manuals and instruct users to configure the Central Management System (CMS) with this IP address within their internal networks. In addition, the upgrade flow requires a physical button press during the patient monitor boot process.
This changes the security response from mitigating a targeted cyberespionage threat to addressing a serious vulnerability that could lead to data leaks or malicious firmware updates.
Noam Moshe, Team82 researcher at Claroty, discussed these findings and their implications with 24×7.
24×7: Can you elaborate on how Team82 determined that the issue with the Contec CMS8000 patient monitor stems from insecure design rather than an intentional backdoor?
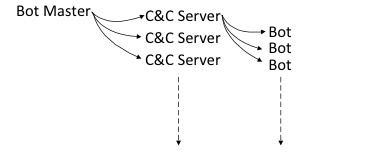
Moshe: After analyzing the Contec CMS8000 patient monitor, our team identified the issue as stemming from insecure design, particularly in the firmware upgrade mechanism. The device fetches firmware updates from a hardcode, publicly routable IP address via an insecure protocol (NFS), which allows anyone controlling the IP to supply malicious binaries. This design flaw reveals the lack of secure design rather than an intentional backdoor.
Throughout our research, we found several factors pointing to poor design choices rather than malicious intent. The main one being the vendor and resellers openly list the IP address in their manuals and instruct users to configure the CMS accordingly. The firmware upgrade process also requires a physical button press during the device’s boot process, which is not a characteristic of a backdoor. These findings collectively indicate that the vulnerabilities stem from flawed design rather than deliberate actions.
24×7: What are the most critical security risks posed by these design flaws, and how might they impact patient data or hospital networks?
Moshe: The design flaws found pose several critical security risks. Unauthorized access allows attackers to gain full control over devices by introducing malicious binaries during firmware upgrades. These vulnerabilities can lead to network compromise, enabling attackers to infiltrate hospital systems and access sensitive patient information, including personally identifiable information and protected health information. It is the use of insecure protocols, like NFS, that make the system susceptible to main-in-the-middle attacks, where data can be intercepted and manipulated during firmware updates. These risks collectively result in severe consequences, including data breaches, disrupted patient care, and potential harm to patients.
24×7: Given that the CMS8000 has been flagged in CISA and FDA alerts, how should healthcare providers interpret these findings in terms of compliance and regulatory response?
Moshe: This should come as a call to action for healthcare providers to prioritize cybersecurity in their medical device ecosystems. These alerts signal the need to take proactive steps to ensure compliance and minimize risks. Providers should start by conducting comprehensive risk assessments to evaluate the security of their devices and networks. Implementing robust security controls, such as network segmentation, vulnerability detection, and patch management processes, is critical to safeguard sensitive patient data and operational systems. Establishing continuous monitoring and well-defined incident response plans will enable healthcare organizations to detect and respond effectively to potential threats, aligning with regulatory expectations and ensuring patient safety.
24×7: What specific steps should hospitals and healthcare organizations take to mitigate the vulnerabilities identified in your research?
Moshe: By adopting a proactive and multi-layered approach to cybersecurity, healthcare organizations can learn to better identify and mitigate these vulnerabilities. Network segmentation should be implemented to isolate medical devices from other network segments, minimizing the potential spread and impact of a breach. Firmware validation is essential, ensuring that upgrades are sourced only from trusted providers and thoroughly validated for integrity before installation.
Providing security training for medical engineers and IT staff is equally important, equipping them with knowledge of secure device management and awareness of emerging threats. Finally, maintaining regular updates by applying the latest security patches and firmware updates will help protect against known vulnerabilities and reduce the risk of exploitation.
24×7: Are these types of insecure design flaws common in medical devices, and what can manufacturers do to prevent similar security risks in the future?
Moshe: Insecure design flaws are relatively common in medical devices due to their complexity and the specialized nature of these devices. Manufacturers can prevent similar security risks in the future by adopting secure development practices, such as incorporating security measures during the design and development phases. Regular security audits are also crucial to identify and address vulnerabilities in a timely manner. Collaborating with cybersecurity experts can help in identifying and mitigating potential risks early in the process, ensuring a more secure final product.
24×7: How is Claroty working with regulators, device manufacturers, or healthcare providers to address these security concerns and improve medical device cybersecurity?
Moshe: Our focus is aimed at enhancing the security of healthcare environments and protecting patient safety by addressing critical challenges in medical device cybersecurity. Through close collaboration with regulators, device manufacturers, and healthcare providers, we deliver research and actionable insights, contribute to the development of industry standards and best practices, and provide robust security solutions designed to protect medical devices and their networks. The primary goal is to strengthen the overall cybersecurity posture of healthcare systems, ensuring safe and resilient care environments for patients.
ID 70926704 | Backdoor Cybersecurity © Michael Borgers | Dreamstime.com