By John Bethune
Health industry data are most often compromised by theft or loss, insider misuse, or miscellaneous error, according to a new report from Verizon security researchers released on April 22.
Of the more than 19 industries covered by Verizon’s 2014 Data Breach Investigations Report, healthcare has been relatively unscathed by security incidents. It accounted for just 26 of the more than 63,000 reported breaches researchers analyzed in 2013.
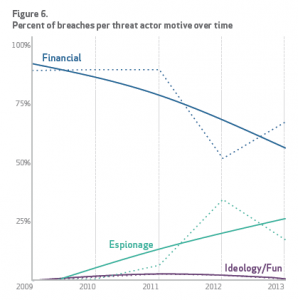
Financial motivations are trending down as a cause of security breaches. Data Breaches by Industry. Source: Verizon 2014 Data Breach Investigations Report. (Click to Enlarge)
However, that may change soon, says Tony Maupin, Verizon’s director for security sales engineering & cloud services. In the past, he says, the main motivation for cybercriminals was financial. But that’s changing: “The trend is not about following dollars anymore. The trend is about following information. And that’s where the medical industry needs to start being concerned … because healthcare tends to have a lot of information.” What’s more, he adds, healthcare enterprises generally “don’t have a lot of investment in technology, so it concerns me that they may end up being a target.”
This year, the seventh that Verizon has published its security report, researchers were able to analyze a decade of data on security breaches and determine nine types of patterns that account for more than 90% of incidents:
- Miscellaneous errors (eg, sending an email to the wrong person);
- Crimeware (various malware aimed at gaining control of systems);
- Insider misuse of privileges;
- Physical theft or loss;
- Attacks on web applications;
- Denial of service attacks;
- Cyber espionage;
- Point-of-sale intrusions; and
- Payment card skimmers.
The report analyzes how each industry is affected by these nine types of incidents and offers strategies for mitigating vulnerabilities. For the healthcare industry, researchers found that nearly half the incidents (46%) were a result of theft or loss of devices such as laptop computers—a higher percentage than for any of the other industries covered. The next most frequent type of incident, accounting for 15% of the total, was related to insider misuse of data access privileges. The third most common type (12%) was miscellaneous error.
The report dedicates several pages of discussion to each type of problem, offering actions that can reduce the likelihood of experiencing that type of breach. To address theft and loss, for instance, the report recommends encrypting devices, encouraging employees to maintain close watch over the devices when in their possession, to back up the devices frequently, and to lock them down when possible.
After reading the report, Maupin says, healthcare executives will realize that, “We need to have security controls in place around our backups, around our staff, and around data-loss prevention—because those are solutions to help remediate the security incidents that we’ve been finding.”
According to Maupin, the Verizon report is based on many more contributors of data on security breaches than ever before. “This year, we have 50 global contributors; last year, we had 18. In 2012, we had five.” Likewise, the number of breaches collected this year has grown dramatically, he says. “In 2013, we had 63,000 incidents, more than we’ve ever had before. It’s double what we had last year.”
The 2014 security report may be downloaded in full at www.verizonenterprise.com/DBIR/2014.
John Bethune is editorial director of 24×7. For more information, contact [email protected].




