
Jeff Kabachinski
I am a little nervous about using the Web. Using a password with a credit card or making my computer available via the Internet worries me. The stories are rampant about stolen identities, ravaged bank accounts, and credit card fraud. I think that overall we have all become attuned to being safe—never giving your social security number to someone asking for it via e-mail, for example. We know that the bad guys cloak themselves by using the look and feel of a real company, bank, or government Web site. We also know not to give out personal information to a caller you do not know. The sneakiest are the bad guys that find a back-door entry to your computer and steal information or just cause trouble. Such means include wiretapping, phishing, keystroke logging, social engineering, dumpster diving, side-channel attacks, and exploiting software vulnerabilities. A password search could be performed by a Java applet on a popular Web site where thousands of Web site visitors may be giving computation power to crack a password without even knowing it.
In health care, there are so many connected systems that hospital staff of all levels and kinds—service and clinical—should exercise good practices in generating their password. To that end, this month’s column concerns online security and talks about the simple things you can do to make sure you have a robust password for everything you need a password for. My list of passwords is currently 83 long—and that is just personal, nonwork-related passwords! Sometimes I think I need a password for my toaster.
It is hard to come up with a password that is easily remembered but also hard to crack. I never really thought about a serious e-mail password since there is no national business discussed in my e-mail. Then I read about how hackers determine your online bank via e-mail correspondence—especially when you forget your password and the bank sends a new one via e-mail.
Cracking Times

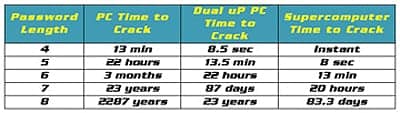
Consider the accompanying table. It will give you an idea of how long one ordinary Pentium PC (that can test a measly 100,000 attempts per second) takes to crack a password that uses all 96 characters (96 = 52 alpha upper and lower case alphabet plus 10 numbers plus 34 special characters such as @, #, $, %). The next column shows that for a fast PC with dual processors, the time diminishes as cracking speeds are at 10 million password attempts per second. Finally, a supercomputer running one billion attempts per second is shown in the last column. The supercomputer can also be many individual PCs working together in a distributed computing scenario—these are the serious hackers with botnets as mentioned earlier. Nine years ago distributed.net successfully used 300,000 different computers to generate an estimated 12 billion passwords per second—9 years ago!
A side note, you can extend the table to show longer password crack times by multiplying each “time to crack” by 96 (the number of available characters). For example, a nine-character password would take a supercomputer 7,968 days.
Consider also that these are brute force hacks where each of the 96 characters is tried in every location. Serious hackers can also use dictionary hacks, where they try each word in the dictionary. These hacking dictionaries will also contain common names and places. In addition, they attempt the most popular characters first. For example, one study (of more than 3 million eight-character passwords) showed that the letter “e” was used 1.5 million times, while the letter “f” was used only 250,000 times. The average character distribution occurred about 900,000 times. The number 1 is the most common number, and the most common letters are a, e, o, and r. Finally, the table shows worse-case times. On average, a hacker will need to try about half the possible passwords before guessing correctly. These more common methods of password cracking (dictionary attacks, pattern checking, and word list substitution) try to reduce the number of attempts required and will usually be attempted before brute force. The end result is that your passwords are at risk, and who would want hackers to have access to their bank account or hospital network?
I hoped I scared you enough. The good news is that passwords can be made strong by using some simple ideas. The strength of a password boils down to a function of length, complexity, and randomness.
Choosing Strong Passwords
The safest method for choosing strong passwords is to use a randomly generated or seemingly random password that:
- Is at least six characters long, and the longer the better. It might make your current passwords longer, but it is worth it. Users rarely make full use of larger characters sets in forming passwords. For example, hacking results from a phishing scheme in 2006 revealed that only 8.3% of users had mixed case, numbers, and symbols!;
- Uses a mix of lesser-used upper- and lower-case letters—with upper case in the middle of the password;
- Does not use any personal information (pet’s name, street names, birthdays, etc);
- Includes the entire 96-character set with numerals, special characters, and punctuation; and
- Does not use any dictionary word.
Examples of strong passwords include: Zf7&ck, 4cv#lkD, g$46Yq. Create a mnemonic to memorize the password to your password list.
In addition, a good policy would be to set password expiration to 30 days. This is based on an eight-character password that can be cracked within 42 days (or half the max 83 days a distributed computer system would use). Be sure that the new password is just as strong!
A Few Don’ts
Do not use “password” as your password! Or drowssap (password backward), letmein, qwerty, asdf, or 123456. Other common passwords to avoid can be seen at www.searchlores.org/commonpass1.htm. I was shocked to see my main password in this list! Do not use the same password for more than one online resource as it can also be a dangerous practice. Do not write your main password on a Post-it note located on the back of your keyboard!
The Bottom Line
A dozen computers working for a week might not be acceptable for a hacker to gain access to your hard drive. Sifting through all that data for any valuable personal information may not be worth the trouble. However, the hacker would use a dozen computers for a week if the outcome is the password to your savings account!
The advice is to use good judgment and don’t be lazy. Regularly changing a password using the list above is fast and painless compared to identity theft and all the losses that can result!
Jeff Kabachinski, MS-T, BS-ETE, MCNE, has more than 20 years of experience as an organizational development and training professional. Visit his Web site at kabachinski.vpweb.com. For more information, contact .




